How to Access API Keys, DB Credentials, from AWS Secrets Manager in AWS Lambda.
Table of contents
No headings in the article.
Introduction:
AWS Secrets Manager is a powerful service provided by Amazon Web Services (AWS) that allows you to securely store and manage sensitive information such as API keys, database credentials, and other secrets.
In this article, I will guide you through the step-by-step process of accessing API keys and database credentials from AWS Secrets Manager within an AWS Lambda function. This approach ensures that your sensitive information remains secure and easily manageable.
Lambda and Secrets Manager
Prerequisites:
Before diving into the steps, you should have
Basic understanding of AWS Lambda, AWS Secrets Manager, and the AWS Management Console.
Additionally, make sure you have an AWS account
The necessary permissions to create and manage AWS Lambda functions and Secrets Manager secrets.
Step 1: Create a Secret in AWS Secrets Manager
We will create two API keys in the secrets manager: dev and prod
Open the AWS Secrets Manager service from the AWS Management Console.
Click on “Store a new secret” to create a new secret.
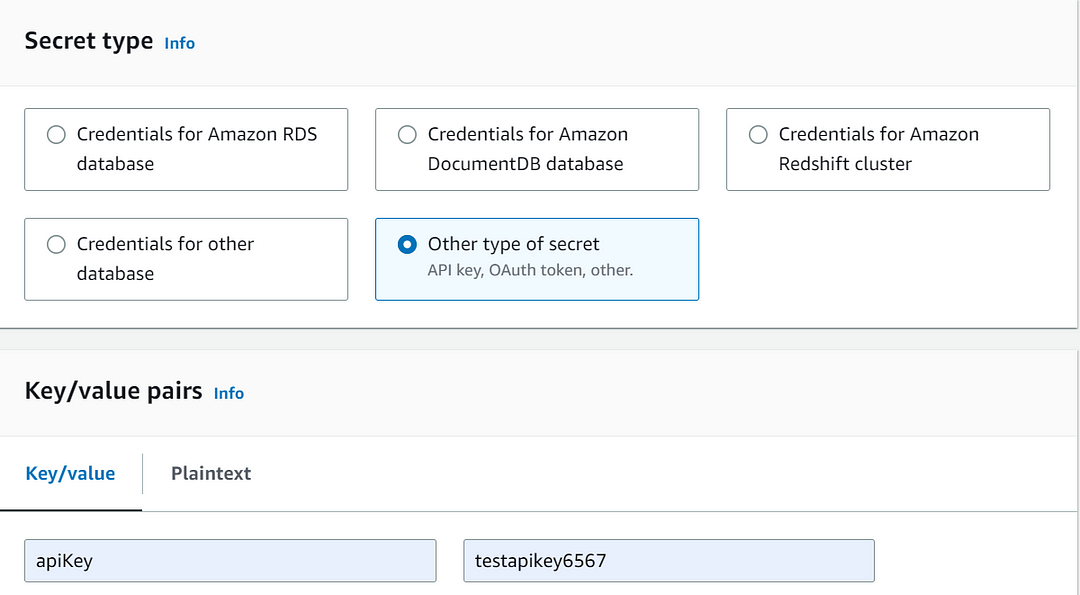
Since we are creating API keys, select “Other type of Secret”.
Enter the secret’s key-value pairs, such as API keys, database credentials, or any other sensitive information you want to store as shown below:
3. Configure the secret settings and permissions as per your requirements as shown below:

Secret type
4. Click on “Store” to create the secret.
You can repeat the same steps for the creation of the second API key for the prod environment.
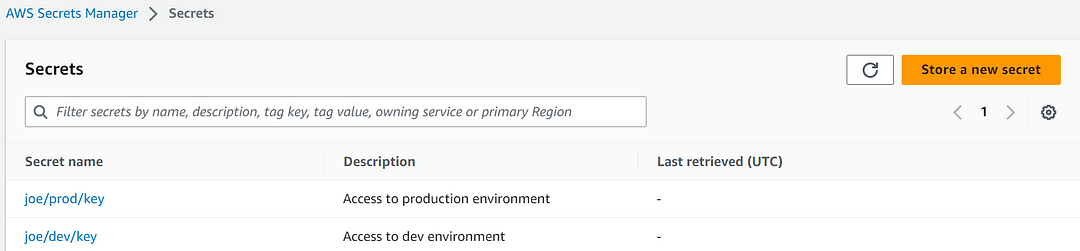
API keys for the dev and Prod environment
Step 2: Configure Lambda Function to Access Secrets.
- First, we need to create an IAM role for the Lambda Function to access the keys. Navigate to “IAM” on your portal, Create a Policy to allow only read access as shown below:
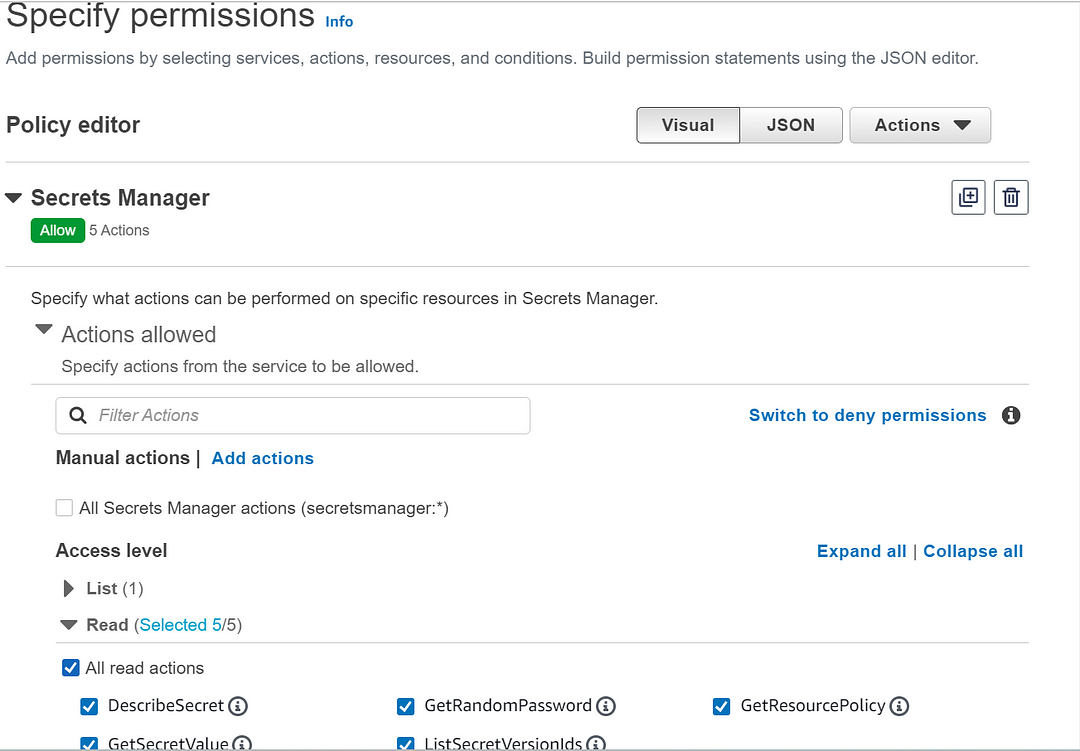
- Specify the resource ARNs
To retrieve the ARNs of the keys, navigate to the keys we created earlier in the secret manager.
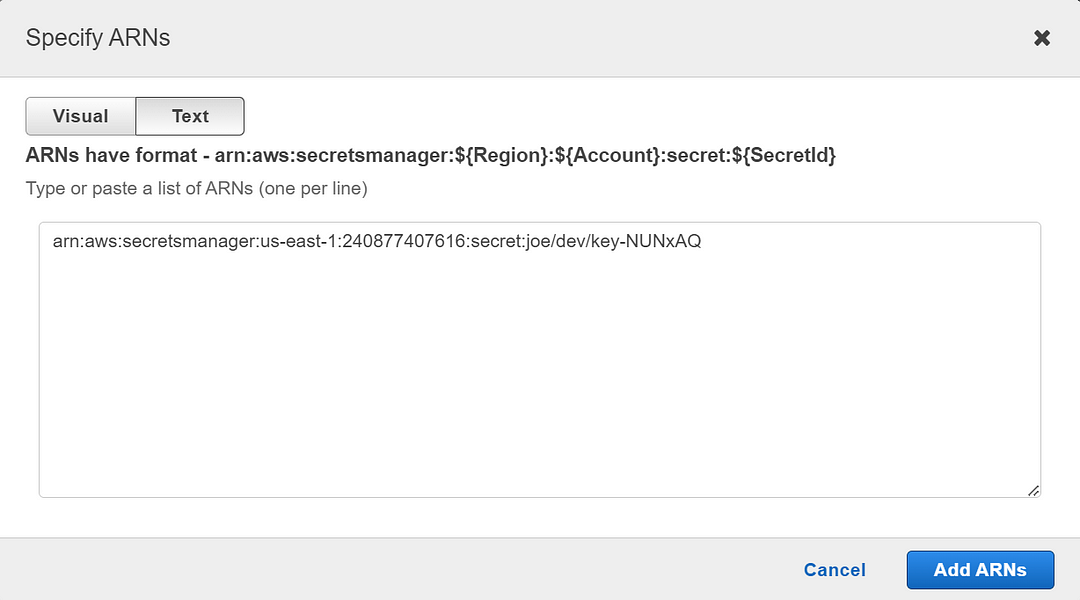
Add ARNs of keys
Give the policy a name, “SecretManagerTestPolicy” and create the policy.
Now we have a policy that has read access to only the two keys we created in the Secrets Manager.
Next, we will add the policy to an IAM role. Create an IAM role as shown below:
Select the AWS service and Lambda as the Use Case, then click Next -> Search for the “SecretManagerTestPolicy” and press Enter.
Select the “SecretManagerTestPolicy” -> Click Next -> Enter a role name “SecretManagerTestRole” -> Click Create.Now the SecretManagerTestRole has been created for the Lambda Function.
Next, Create the lambda function:
In the AWS Lambda function configuration page, enter the following details as shown below:
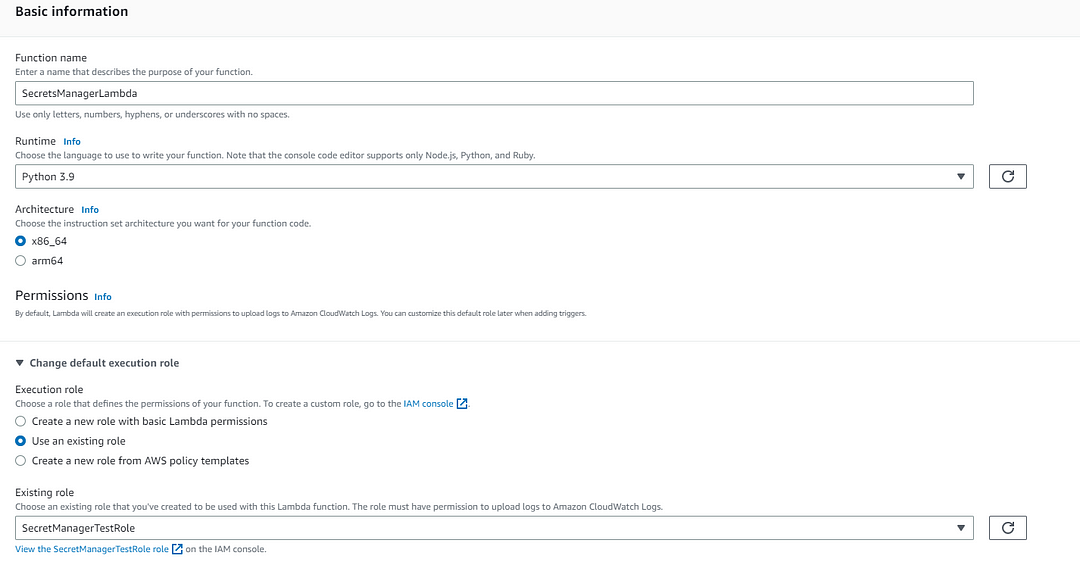
Lambda function for Secret Manager
And Click the Create button, the lambda function will be created as shown below:
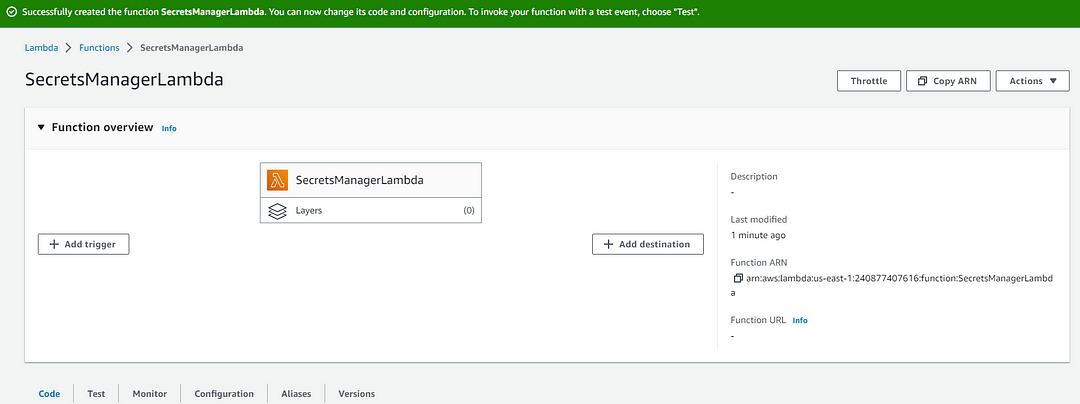
Lambda function
Next, let's understand the Python code for the lambda function:
Importing Required Modules:
import json
import boto3
import base64
from botocore.exceptions import ClientError
This code imports the necessary modules required for the Lambda function to work:
json: Used for JSON operations, such as loading JSON strings into Python objects.boto3: The AWS SDK for Python, used to interact with AWS services.base64: Provides functions to encode and decode binary data as Base64.ClientErrorfrombotocore.exceptions: Allows handling specific errors raised by AWS service clients.
Defining the Lambda Handler:
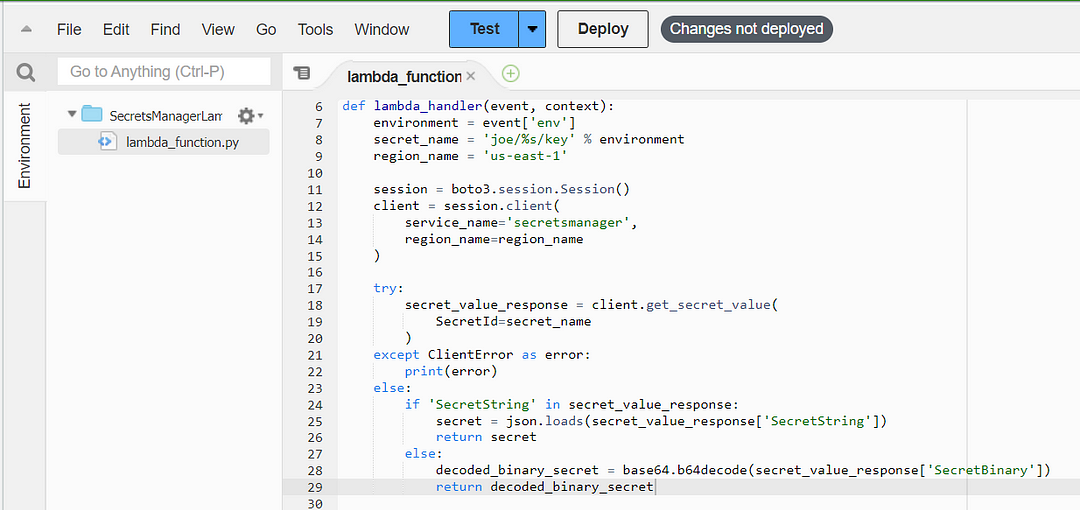
def lambda_handler(event, context):
This is the entry point of the Lambda function. The function takes in two parameters:
event: A dictionary containing information about the triggering event.context: A context object providing information about the runtime environment.
Extracting Environment and Secret Information:
environment = event[‘env’]
secret_name = ‘joe/%s/key’ % environment
region_name = ‘us-east-1’
Here, the code extracts the value of the 'env' key from the event dictionary. This key is expected to contain environmental information. The secret_name variable is then constructed using the extracted environment value. Additionally, the region_name is set to 'us-east-1', which specifies the AWS region where the Secrets Manager service is located.
Creating a Session and Client:
session = boto3.session.Session()
client = session.client(
service_name=’secretsmanager’,
region_name=region_name
)
A new session object is created using boto3.session.Session(). Then, a client object for the Secrets Manager service is instantiated using the session's client() method. The client is configured with the specified service name and region.
Retrieving the Secret Value:
try:
secret_value_response = client.get_secret_value(
SecretId=secret_name
)
except ClientError as error:
print(error)
Handling the Secret Value:
else:
if ‘SecretString’ in secret_value_response:
secret = json.loads(secret_value_response[‘SecretString’])
return secret
else:
decoded_binary_secret = base64.b64decode(secret_value_response[‘SecretBinary’])
return decoded_binary_secret
If the secret value is successfully retrieved, the code checks if it is in string format by looking for the 'SecretString' key in the secret_value_response dictionary. If it exists, it means the secret value is in JSON format, and the code uses json.loads() to load it into a Python object before returning it.
If the secret value is not in string format, it is assumed to be in binary format, and the code uses base64.b64decode() to decode it from Base64 before returning the decoded binary secret.
Step 3: Test and Deploy the Lambda Function
Finally, let's combine the code as shown below. Click on the “Test” button in the top-right corner of the AWS Lambda configuration page to test your function.
Lambda function
- Configure test event inputs as per your function’s requirements and execute the test.
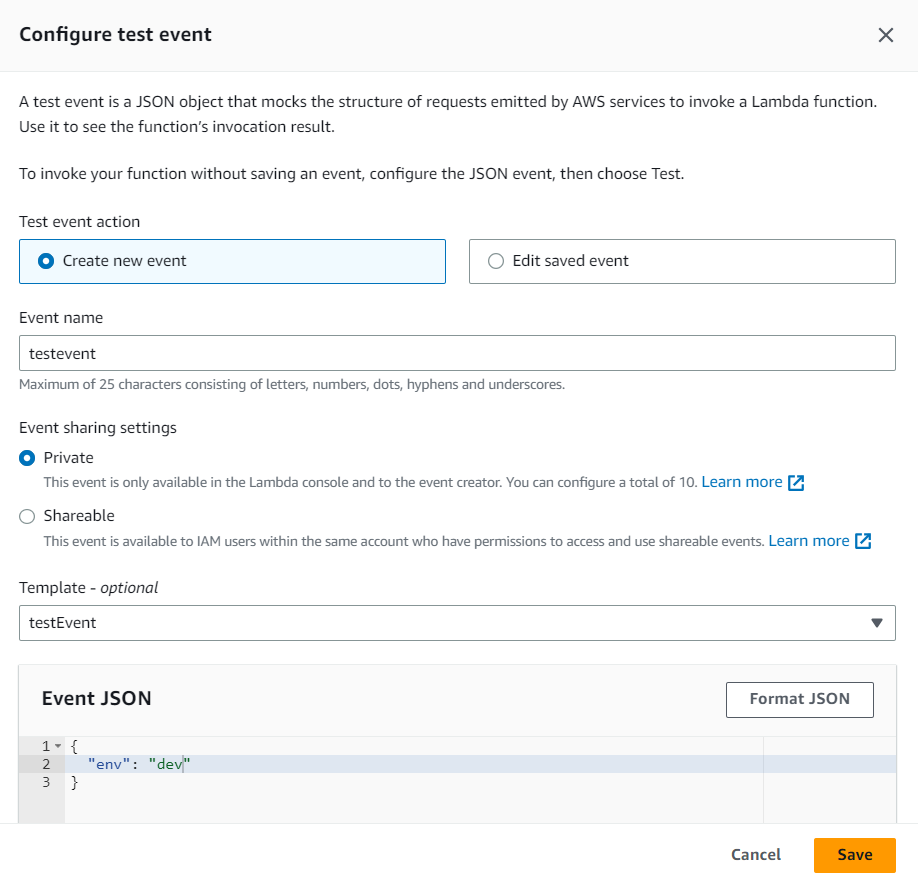
- Click on the “Deploy” button to deploy your Lambda function and Click on “Test”. Verify that your function retrieves the secrets correctly and operates as expected.
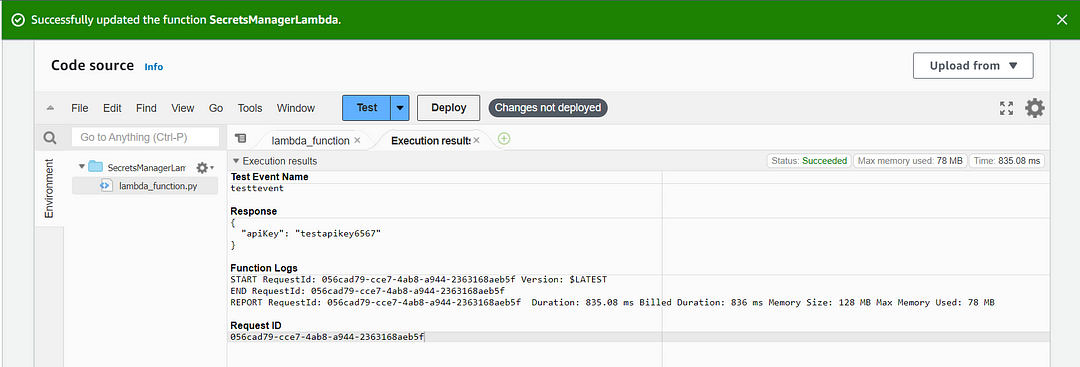
Conclusion:
In today's digital landscape, the security and management of sensitive information are paramount. AWS Secrets Manager, combined with AWS Lambda, provides an elegant and secure solution for accessing API keys, database credentials, and other secrets within your applications.
By following the step-by-step guide outlined in this article, you can seamlessly integrate AWS Secrets Manager into your AWS Lambda functions. This ensures that your sensitive information remains protected, reducing the risk of unauthorized access or exposure.
Also, remember to adhere to security best practices, such as implementing least privilege access and securely handling retrieved secrets within your Lambda function code. Regularly review and rotate your secrets to further enhance the security posture of your applications.
Thank you for reading.